End-User Technology Training
A perk of having a business partnership with us is that you will have the ability and accessibility to our resources and knowledge base ranging from security, compliance, data backup, applications, solutions and many more areas. Our digital education can be applied through various technologies and comes extremely handy during new implementations. This is not the opportunity to lecture you on what you do right or wrong. It is rather to keep you aware of trends and how to use a particular new technology that may give you a competitive advantage. If a new service may benefit you, it is best to inform you in advance before the next budget period. When the time is right to adopt the new solution, you would already be aware of the benefits.

Overview

Training of the end-users is one of the most important steps for successful system implementation and system, adaptation. Training has two sides - it has a cost, but it offers many benefits. To justify the costs, we understand that you must be able to quantify the benefits. Training benefits can exist at many levels, including increased productivity, lowered internal support costs and delivering time which can be dedicated to roadmaps and new implementations. Whatever the specifics may be, these costs and benefits are directly tied to specific business needs and results. i.e. What are you looking to achieve and will training provide it? At the end of the day, training initiatives brings a complete and comprehensive value to business needs, costs and processes.
Ensure Employee Privacy with Adjustable Tracking
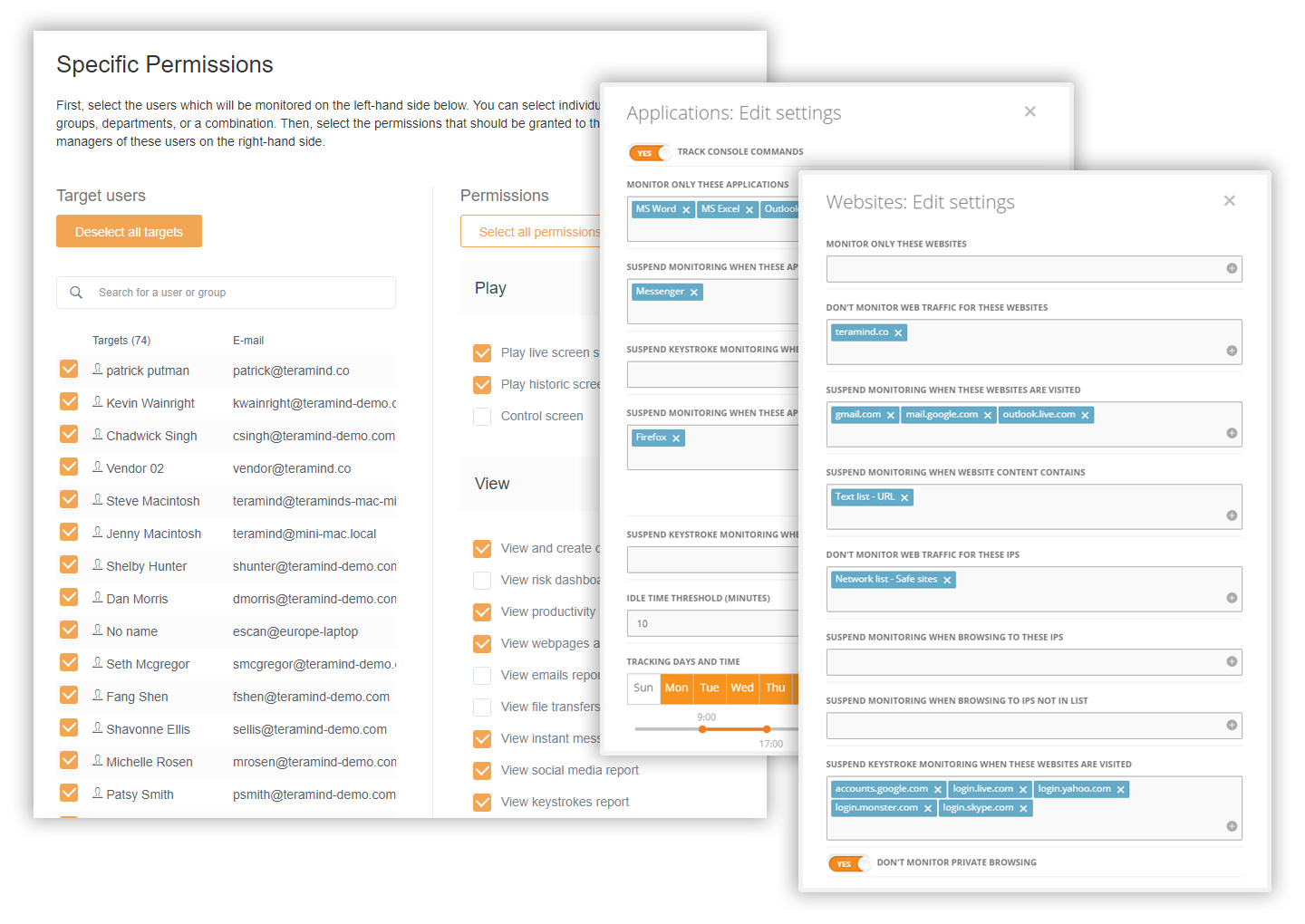
Each monitored object like screen/apps/websites etc. can be configured to take into consideration what needs to be monitored and measured and who has access to the monitored records. You can control who you want to monitor, how much you want to monitor, when and for how long. This allows for instant administrative control to respect employee privacy requirements.
Detect Insider Threats with Intelligent Policy & Rules Engine
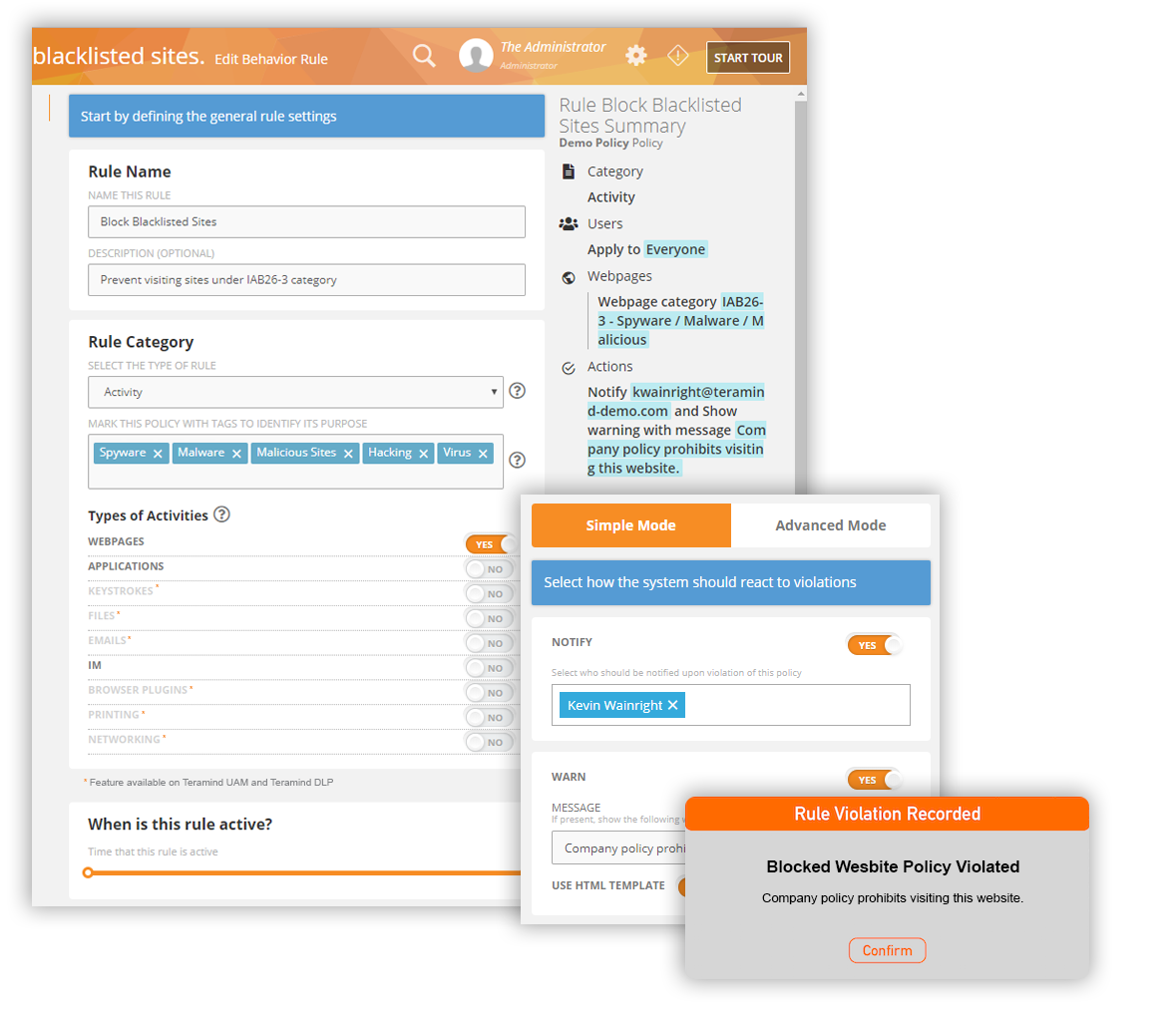
Determine what behaviours are high risk i.e. downloading files and attachments from an unknown website, running a risky application etc. Then, apply behaviour-based rules to detect when users violate the rules. The system will automatically block harmful employee activity or warn the user with a customised message about potential danger reducing false positives with minimal supervision. The system can also notify you about sensitive rule violation incidents that need your personal attention.
Boost Employee Productivity and Increase Organisational Performance
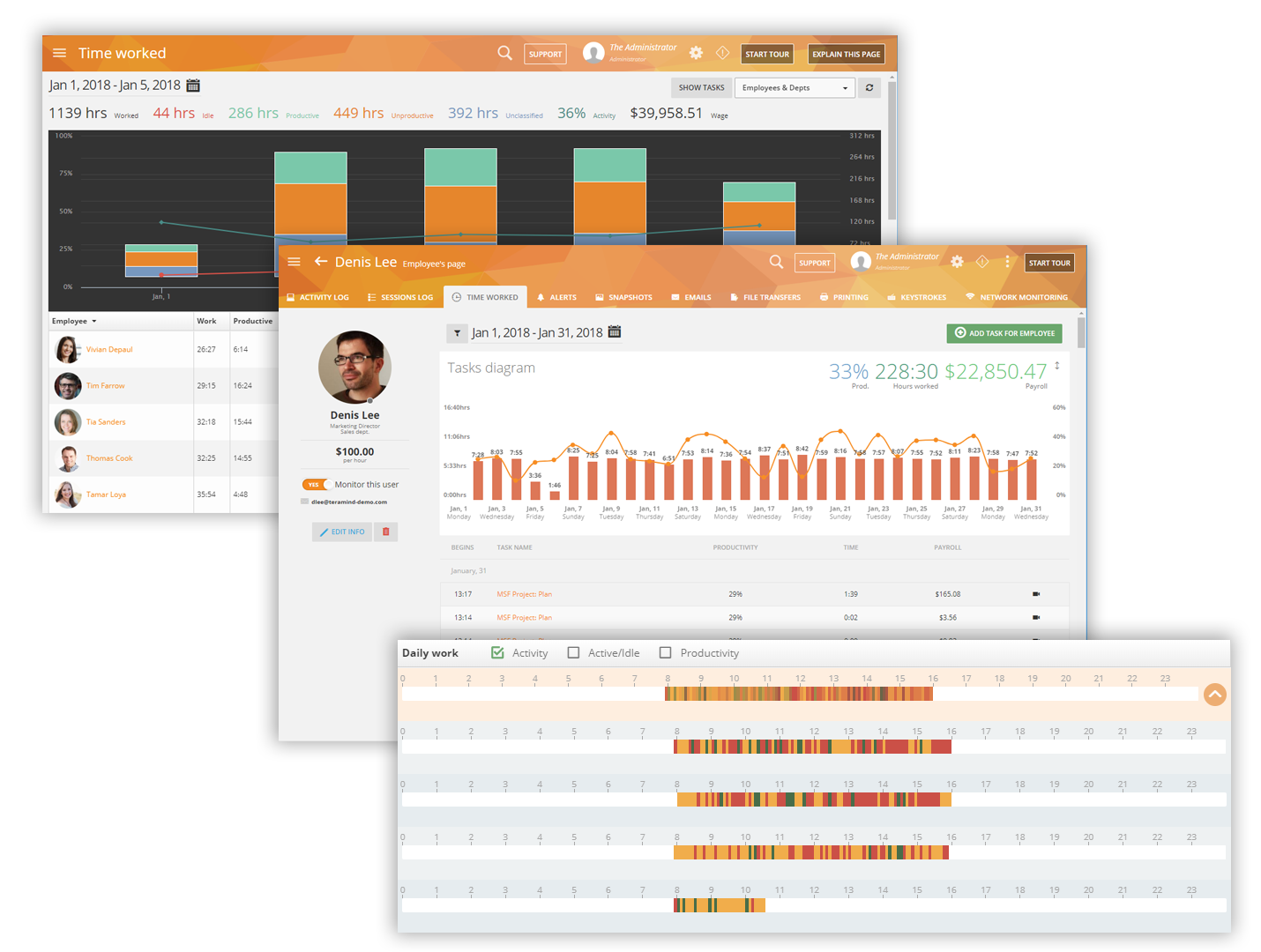
Use the workforce productivity tools to track active vs inactive time, late shifts, long breaks, etc. Use intelligent activity-based rules to automatically identify clues to customer dissatisfaction (angry sentiments in social media posts/customer query in instant messenger not answered etc.) and implement processes to provide better service.
Monitor Privileged Users for Extra Security
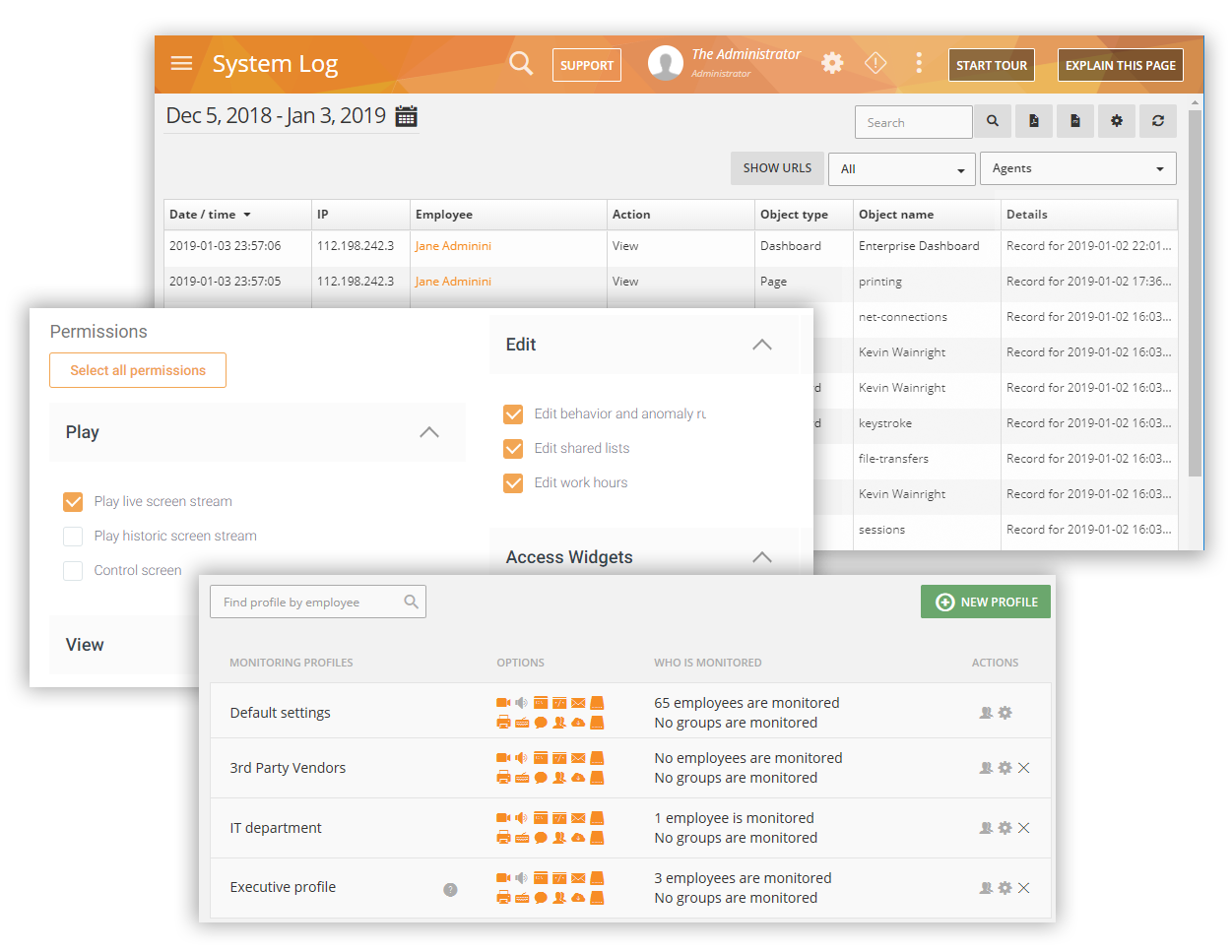
Teramind allows organisations to create profiles for remote and privileged employees and then define what information and system resources each profile can access. Create autonomous rules to notify the authorities of any suspicious privileged user activity, such as unscheduled login, access to system configuration, creation of backdoor accounts, etc.
Audit Security Incidents with Forensics
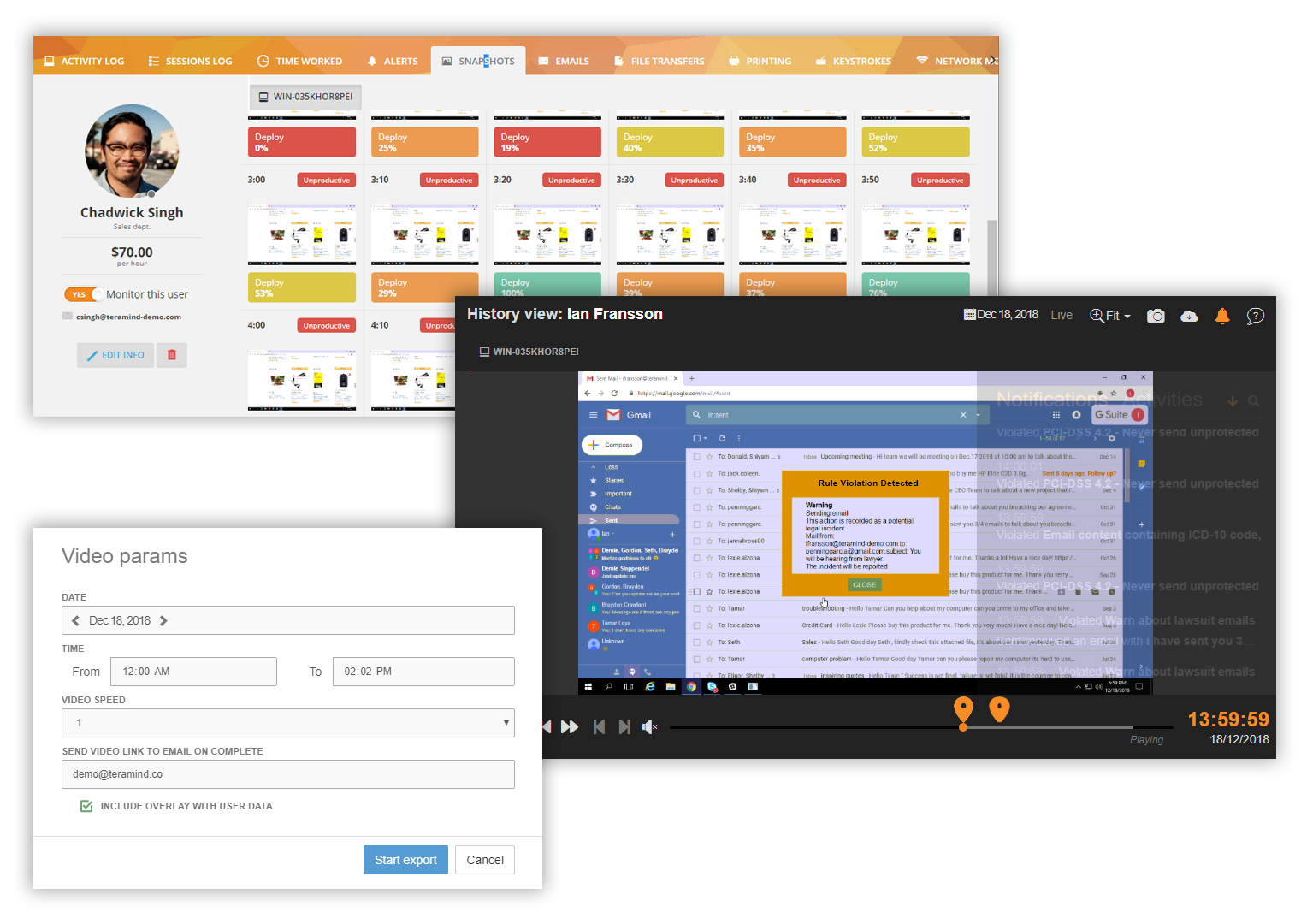
Detailed alerts for all users can be viewed including any security event and what action was taken, which app/site was involved, what data got accesses etc. Session recordings and history playback can be used to view user’s desktop or exported as MP4 video to be used as evidence in any investigation. Immutable system logs and session reports provide with further information to trace back to the source and cause of any security incident.
Talk to an expert
We'd love the opportunity to sit with you and discuss technology and your business
