He has done it again. Two months ago a “security researcher” who goes by the Twitter alias @SandBoxEscaper publicly dropped a zero-day exploit which showed a vulnerability residing within the Microsoft Jet Database Engine which allows an attacker to remotely execute malicious code on any vulnerable windows computer. Yesterday @SandboxEscaper did it again by releasing another proof-of-concept exploit for a new Windows zero-day vulnerability.
SandBoxEscaper has posted a link to a Github page hosting a proof-of-concept (PoC) exploit for the vulnerability that appears to be a privilege escalation flaw residing in Microsoft Data Sharing (dssvc.dII). This data sharing service runs as a LocalSystem account that provides brokering between applications whilst also giving extensive privileges.
The Data Sharing Service (DSS) provides data brokering between applications along with a local service that runs as LocalSystem account with extensive privileges.
Why Should I Be Worried?
This flaw will allow a low-privileged attacker to elevate privileges on a target system, though the PoC exploit code (deletebug.exe) released by the “researcher” only allows a low privileged user to delete critical system files – that otherwise would only be possible via admin level privileges.
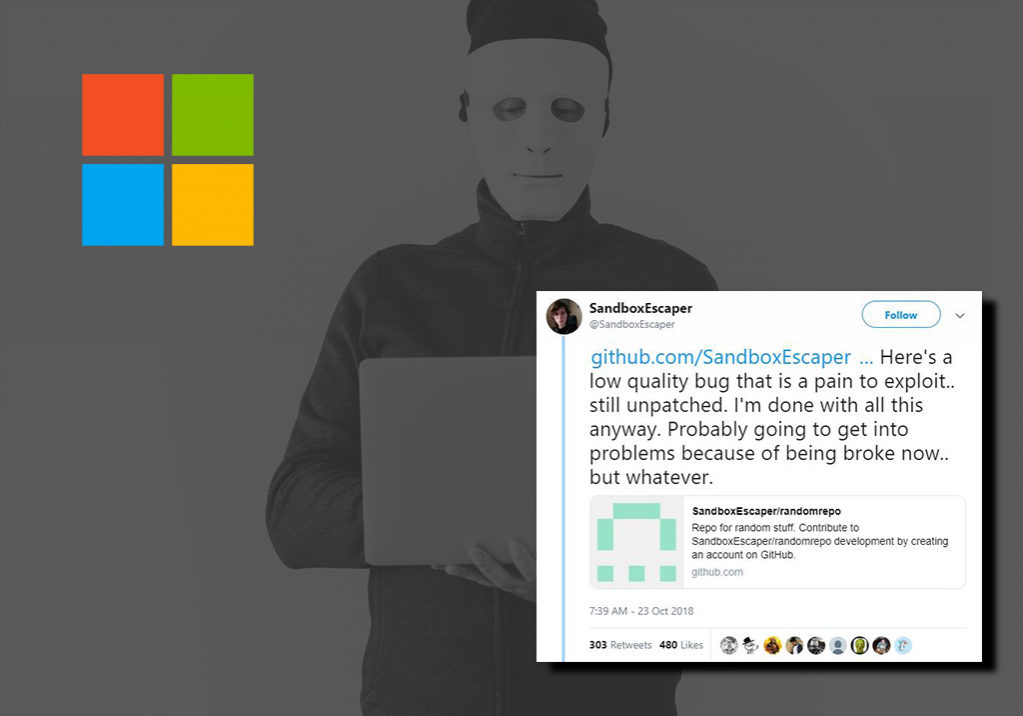
“Not the same bug I posted a while back, this doesn’t write garbage to files but actually deletes them.. meaning you can delete application dll’s and hope they go look for them in user write-able locations. Or delete stuff used by system services c:\windows\temp and hijack them,” the researcher wrote.
There is one positive (sort of) this vulnerability does not affect later versions of Windows operating systems including 7 or 8.1. 👏👏👏👏👏
This PoC exploit has successfully been tested against fully-patched Windows 10 systems:
Confirmed as well on Win10 1803, fully-patched as of October.
It’s perhaps worth noting that the service used by the PoC, Data Sharing Service (dssvc.dll), does not seem to be present on Windows 8.1 and earlier systems. https://t.co/W8cNNC4xYO— Will Dormann (@wdormann) October 23, 2018
Not only has SandBoxEscaper leaked a second Windows zero-day vulnerability in less than two months, but this irresponsibility has also once again left all Windows users vulnerable to hackers until the next month’s security patch Tuesday, which is scheduled for November 13 2018.
If you need assistance please contact us as soon as possible.
Other Articles That May Interest You:














Share your thoughts in the Comments section: