The ongoing battle of innovation and advancement between cyber-criminal and security industries means that we, as a company, need to provide our customers a balanced view of the Global Cyber Arms Race. We believe that by providing an in-depth understanding and insight of the threat environment, the desired outcome is to give a deep consultative security engagement with our customers so you all can gain more confidence in our ability to protect you and your investments.
The modern Cyber arms race – against governments, businesses and individuals alike – is comprised of a series of attacks, counterattacks and respective defensive counter measures. It does not matter what size your organisation is, large or small, everybody is caught in the middle of a global cyber arms race with vastly difference resources.
3 Things We Know
- A Tech Patrol customer on average would have missed 900 attacks per year hidden by TLS/SSL encryption. Firewalls must have the capability to see into encrypted traffic to stop hidden threats.
- Ransomware is still the malware of choice in attack campaigns by Cybercriminals as they are constantly retooling their ransomware payload to be more stealthy, aggressive (with payment demands) and profitable.
- Memory-based attacks are the next battleground, and will take advanced security to effectively defend against it. Cybercriminals are already leveraging these types of vulnerabilities and exploits.
Why should you care about these things? To increase confidence and assurance for you (if not going through Tech Patrol) to make informed decisions and take calculated actions towards a successful cyber defense strategy based on relevant threat data and analysis.
Security Industry Advances
[smartslider3 slider=5]Cyber Criminal Advances
[smartslider3 slider=6]Deeper Analysis: Security Industry Advances
Key Point To Highlight:
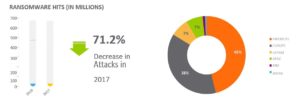
- Ransomware showed incredible signs of momentum in the 4th quarter of 2016. The trending data suggested it would likely extend into 2017.
- However 2017 did not turn out as trending data suggested. In fact, ransomware attacks actually dropped sharply by 70%.
- Even with the headlines made by WannaCry, Petya, NotPetya and Bad Rabbit, full year’s data shows ransomware attacks decrease from 638 million to 184 million between 2016 and 2017.
Explanation why:
- Ransomware remains the malware of choice, and SonicWall can only speculate that the decline in ransomware attacks may be attributed to the following:
- After examining and comparing a number of unique bitcoin wallets belonging to WannaCr and Crytolocker, SonicWall Capture Labs researchers found that transactions via ransomware-related wallet addresses dropped significantly in 2017.
- Fewer People paid:
- Adoption of better ransomware security and data recovery solutions
- The inability of hackers to provide keys and recover data. Why pay if they won’t give you back your data. Bad business move by hackers.
Key Point To Highlight:
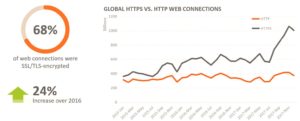
- Through 2017, we continue to observed strong growth in TLS/SSL-encrypted web connections with 24% increase over 2016.
- Total volume accounted for 68% of overall web connections.
- We attributed this growth to the growing use of secured cloud applications and websites.
TP Caution:
- Although there are many benefits to encrypting web sessions, Tech Patrol observed a less positive trend emerging as hackers exploit this encryption as a way of “hiding” malware from corporate firewalls.
- Cybercriminals are leveraging that same encrypted internet to deliver malware that are unseen by most firewalls.
- This Method of attacks pose greater risks because it’s more difficult to detect.
Exploit Kit Success Declined
Key Point To Highlight:
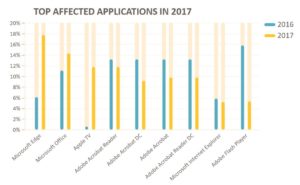
- Newer versions of Exploit Kits (EK) did not have the same level of effectiveness as previous EKs had when Adobe Flash was a popular and easy target application
- With zero critical Flash vulnerabilities discovered in 2017 due to major browsers ending Adobe Flash support, this forces cybercriminals to seek new attack vectors
- Attacks against the most popular Adobe products were down across the board.
- Attacks against Microsoft Office and related applications (e.g., Word, Excel) increased.
- As Microsoft move users to using Edge from IE, we saw a 13 percent increase in attacks against Edge.
TP Caution:
- Malware writers are actively looking to establish a Flash replacement to successfully deploy common exploits.
- Newly developed EKs will evolve and advance to a dangerous level of effectiveness.
Why this matters:
- Its paramount that security systems and services are up to date to handle any zero-day attacks against these targeted applications.
The Solution:
- Capture ATP cloud-based multi-engine sandboxing solution detects and blocks suspicious files until a verdict is rendered and automatically patches all firewalls globally with active security services. If you want to know more about this particular solution that can be applied to our firewall solutions contact us.
Worldwide law enforcement continued to arrest key malware and exploit kit authors in 2017, such as:
Kelihos Botnet – Pyotr Levashov.
Treason (Karpersky Exec) – Ruslan Stoyanov.
vDOS SERVICE – Italy Huri.
Citadel Malware Toolkit – Mark Vartanyan.
Extortion (Attemted DDoS Attack) – Kaymar Jaahanrakhsan.
Kronos Banking Trojan – Marcus Hutchins.
Sakula Malware – Yu Pingan.
vDOS SERVICES – Yarden Bidani.
These arrests made a significant dent in the scale, volume and success of cyber attacks and continues to be disruptive to the malware supply chains. In one of the most high profile cases, Marcus Hutchins, the British security researcher responsible for stumbling onto the WannaCry kill switch, was later arrested in the US for creating the banking Trojan Kronos.
Deeper Analysis: Cyber Criminal Advances
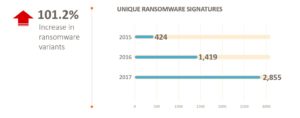
Unique Types of Ransomware Found
Key Point To Highlight:
- Even though the total volume of ransomware attacks was down notably year over year, the number of ransomware variants doubled in 2017.
- We saw a 101.2% increase in the number of unique new variants of ransomware created and used in those attacks.
State the danger:
- Bad actors are constantly retooling their ransomware payload to be more stealthy, aggressive (with payment demands) and profitable, since they are catching fewer victims.
State why it matters to your customers:
- Ransomware is still the malware of choice in attack campaigns by Cyber Criminals.
- Ransomware-as-a-Service (RaaS) usage continues to grow.
- New propagation methods (EternalBlue and Remote Desktop Protocol (RDP) are being used to evade detection.
The Solution:
- Tech Patrol uses machine learning to categorize completely new malware vs a modified version of existing malware.
- Cloud-based multi-engine sandboxing solution detects and blocks suspicious files until a verdict is rendered.
- Automatic patches which all Tech Patrol firewall customers receive with active security services.
SSL/TLS Encryption Hiding Cyber Attacks
Key Point To Highlight:
- For many years, the industry has always relied on 3rd party research and serveys such as Gertner, NSS Labs for their estimate of how much cyber-attacks are hidden inside SSL/TSL encrypted traffic. Although it was guidance data, it was not hard data.
- Tech Patrol’s unique ability to track and log real hard data on attacks hidden inside encrypted web connection, our research saw an average of nearly 5% percent of all file-based malware propagation attempts used TLS/SSL encryption.
- The data was collected from Tech Patrol’s firewall service with active DPI-SSL running.
The Danger:
- With 9.3 billion malware attacks in 2017, this equates to 60 file-based malware propagation attempts per Tech Patrol’s firewall vendor each day.
- It only takes one success attack to take an entire company to its knees.
Why This Matters:
- If your firewall is not inspecting this traffic, you’re actually missing a lot of the value of your firewall.
- Tech Patrol’s Firewall solution customer would on average would have missed 900 attacks per year hidden by TLS/SSL encryption.
- Firewall must see into encrypted traffic to stop hidden threats.
The Solution:
- Tech Patrol’s Deep Packet Inspection of SSL (DPI-SSL) technology stops encrypted threats by decrypting and inspecting encrypted traffic. Make sure your business’ implemented technology does the same.
Key Points To Highlight:
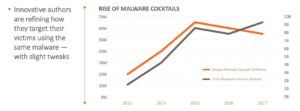
- While we saw an increase in total malware volume, we saw a corresponding decrease in the number of unique malware variants.
- Cyber Criminals continue to optimise existing code to maximise its use and effectiveness.
The Danger:
- Some malware morphs with the main purpose of avoiding detection.
- Our researchers identified versions of Cyrber ransomware being modified as often as twice per day! We call this a “malware cocktail”.
Why This Matters:
- The important question is, can your signature-based security system keep pace? – How do you know?
The Solution:
- Tech Patrol’s technology uses machine learning to categorise completely new malware vs modified version of existing malware.
- Cloud-based Multi-engine sandboxing solution detects and blocks suspicious files until a verdict is rendered.
- Automatically patches all Tech Patrol firewall globally with active security services.
Processor Threats
Meltdown targets modern processor vulnerabilities to steal sensitive data inside protected memory space. Memory Regions are the next key battlegrounds.
“Sandbox techniques are often ineffective when analyzing the most modern malware. SonicWall’s RTDMI technology is very fast and very precise, and can mitigate sophisticated attacks where the malware’s most protected weaponry is exposed for less than 100 nanoseconds.” –John Gmuender, CTO, SonicWall
Key Points To Highlight:
- Google’s Project Zero revealed a serious, harmful processor-based vulnerability known as Meltdown.
- These vulnerabilities execute timing attacks on affected CPUs like those from Intel and AMD.
- Once an attacker gains access to the memory space of the affected CPU, it can read the machine’s entire physical memory.
- Cyber Criminals are already leveraging these types of vulnerabilities and exploits.
The Danger:
- A successful exploit of this vulnerability allows an attacker to access sensitive information such as passwords and emails inside protected memory regions on the processors.
Why This Matters:
- Memory based attacks are the next battleground, and it will take advanced security to protect organizations.
The Solution:
- Security defense must be able to detect and block malware that doesn’t display any malicious behavior and hides its weaponry via custom encryption, which is exposed only for a short time –less than 100 nanoseconds.
- Real-time identification is critical to protect against these advanced attacks.
- Tech Patrol’s SonicWall Capture Cloud with the patent-pending Real-Time Deep Memory Inspection (RTDMI™) technology has proven effective against zero-day threats such as processor-based vulnerabilities like Meltdown
As mentioned, the modern Cyber arms race – against governments, businesses and individuals alike – is comprised of a series of attacks, counterattacks and respective defensive counter measures. It does not matter what size your organisation is, large or small, everybody is caught in the middle of a global cyber arms race with vastly difference resources.
If you don’t know if your business is equipped to handle targeted attacks please contact your CTO, or IT manager or reach out to us today.

















Share your thoughts in the Comments section: