The Adobe network has released new security updates which patches critical vulnerabilities which adobe says that “[the] successful exploitation could lead to arbitrary code execution in the contact of the current user” a statement released on their official security bulletin earlier today.
New versions have been released of it’s Acrobat DC, Reader and Photoshop CC for windows and macOS users for a total of 48 vulnerabilities in it’s software, 47 of which affect Adobe Acrobat and reader applications, and on critical remote code execution flaw has been patched in Adobe Photoshop CC. Out of that 47, Adobe Acrobat and Reader were affected with 24 critical vulnerabilities – categorized as double free, heap overflow, use-after-free, out-of-bound write, type confusion, and Untrusted pointer deference – which if exploited, could allow arbitrary code execution in the context of the targeted user.
Affected Versions
- Acrobat DC
- Consumer
- 2018.011.20038 and earlier versions
- Platform: Windows and macOS
- Acrobat Reader DC
- Consumer
- 2018.011.20038 and earlier versions
- Platform: Windows and macOS
- Acrobat 2017
- Classic 2017
- 2017.011.30079 and earlier versions
- Platform: Windows and macOS
- Acrobat Reader 2017
- Classic 2017
- 2017.011.30079 and earlier versions
- Platform: Windows and macOS
- Acrobat DC
- Classic 2015
- 2015.006.30417 and earlier versions
- Platform: Windows and macOS
- Acrobat Reader DC
- Classic 2015
- 2015.006.30417 and earlier versions
- Platform: Windows and macOS
What are the vulnerabilities?
The rest of the 23 flaws, including NTLM SSO hash theft, Security Bypass, out-of-bounds read and HTTP POST newline injection via XFA submission, are market by Adobe as important and can lead to information disclosure or security bypass.
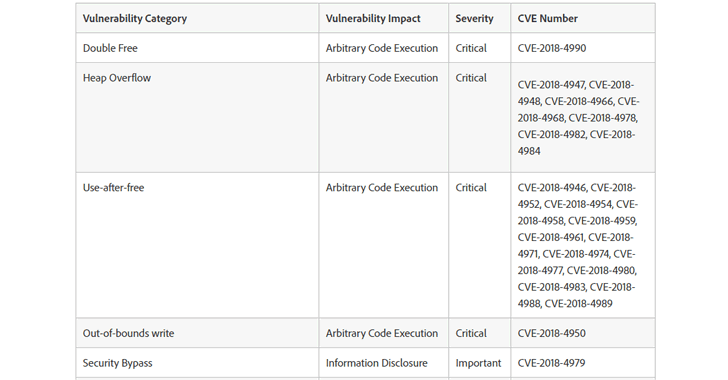

All of the above listed vulnerabilities released by Adobe impact all of the versions listed above. These listed vulnerabilities have been given a priority rating of “1”, meaning that the flaws are either being exploited or are likely to be exploited. So, users are highly recommended to update their software as soon as possible!
Photoshop Security Patches
Photoshop CC 19.1.3 and earlier 19.x versions, as well as 18.1.3 and earlier 18.x versions has been identified to have a critical vulnerability. Adobe has released security patches to directly rectify this critical culnerability, categorized as “out-of-bounds write” issue, which can be exploited to execute arbitrary code in the context of the current user.
The company has credited researcher Giwan Go of Trend Micro’s Zero Day initiative for reporting the flaws, which has been addressed with the release of Photoshop CC2018 v19.1.4. and Photoshop CC 2017 v18.1.4. However, this particular vulnerability has been given a rating of “3”, meaning that it hasn’t been as targeted by hackers.

















Share your thoughts in the Comments section: