Office 365 is an integrated experience of apps and services, designed to assist businesses in collaborative growth by using powerful cloud technology that can enable an employee anywhere in the globe. Microsoft’s O365 package comes with its own securing and compliance solution that can help businesses avoid devastating financial and legal repercussions of data loss. Even with the built-in security service, having your own measures beyond the standard out-the-box is a must and here are some tips on what we do to make sure our client’s office 365 business data is private and secure.
Session Timeouts
were you ever in a session and a colleague called you over or you went on a call and had to leave quickly and forgot to log out? This is something a lot of people do and it gives unfettered access to company accounts, in the wrong hand can be a red alert to sensitive data. Tech Patrol applies session timeout: Session can expire when users are inactive, when they close the browser or tab, or when their authentication token expires for other reasons such as when their password has been reset. There are different types of session timeouts that correspond with the typical use of each service:
| Office 365 service | Session timeout |
|---|---|
| Office 365 Admin center | You are asked to provide credentials for the admin center every 8 hours. |
| SharePoint Online | 5 days of inactivity as long as the users chooses Keep me signed in. If the user accesses SharePoint Online again after 24 or more hours have passed from the previous sign-in, the timeout value is reset to 5 days. |
| Outlook Web App | 6 hours. You can change this value by using the ActivityBasedAuthenticationTimeoutInterval parameter in the Set-OrganizationConfigcmdlet. |
| Azure Active Directory (Used by Office 2013 Windows clients with modern authentication enabled) | Modern authentication uses access tokens and refresh tokens to grant user access to Office 365 resources using Azure Active Directory. An access token is a JSON Web Token provided after a successful authentication and is valid for 1 hour. A refresh token with a longer lifetime is also provided. When access tokens expire, Office clients use a valid refresh token to obtain a new access token. This exchange succeeds if the user’s initial authentication is still valid. Refresh tokens are valid for 90 days, and with continuous use, they can be valid until revoked. Refresh tokens can be invalidated by several events such as : User’s password has changed since the refresh token was issued. An administrator can apply conditional access policies which restrict access to the resource the user is trying to access. |
| SharePoint and OneDrive mobile apps for Android, iOS, and Windows 10 | The default lifetime for the access token is 1 hour. The default max inactive time of the refresh token is 90 days. Learn more about tokens and how to configure token lifetimes To revoke the refresh token, you can reset the user’s Office 365 password |
| Yammer with Office 365 Sign-In | Lifetime of the browser. If users close the browser and access Yammer in a new browser, Yammer will re-authenticate them with Office 365. If users use third-party browsers that cache cookies, they may not need to re-authenticate when they reopen the browser. > [!NOTE]> This is valid only for networks using Office 365 Sign-In for Yammer. |
Policy Alerts
When looking to meet a companies data security obligations it’s always good to establish policy notifications in the Office 365 Compliance Center. You use the new alert policy and alert dashboard tool established in the Office 365 Security & Compliance Center to create alert policies and then view the alerts that are generated when users perform activities that match the conditions of an alert policy. A great example of this is when an employee is looking to send sensitive messages to contacts who aren’t listed in the companies network. They can be alerted by a policy tip (or not) in which it may also educate them on safer data sharing practices.
How alert policies work: via O365
Here’s a quick overview of how alert policies work and the alerts that are triggers when user or admin activity match the conditions of an alert policy.

- An admin in your organization creates, configures, and turns on an alert policy by using the Alert policies page in the Security & Compliance Center. You can also create alert policies by using the New-ProtectionAlert cmdlet in PowerShell.
- A user performs an activity that matches the conditions of an alert policy. In the case of malware attacks, infected email messages sent to users in your organization will trigger an alert.
- Office 365 generates an alert that’s displayed on the View alerts page in the Security & Compliance Center. Also, if email notifications are enabled for the alert policy, Office 365 sends
an notification toa .list recipients - An admin manages alerts in the Security & Compliance Center. Managing alerts consists of assigning an alert status to help track and manage any investigation.
MFA – Multi-factor Authentication
In this day and age you should never reply on just one password, that’s why we are moving further into facial recognition. There are too many businesses being hacked through brute force efforts that lands an employees easy password. To reduce the risk of this for our clients we look towards multi-factor authentication methods that work but isn’t too inconvenient. Hackers now not only need to get the password correct but they also have to establish the second form of authentication that could be as simple as a direct text msg to your phone, that’s recorded on the company network, with a code. Simple, Effective, Stops Hackers.
Setting up multi-factor authentication: via O365
- You must be an Office 365 global admin to do these steps.
- Go to Users > Active users.
- Choose More > Setup Azure multi-factor auth. If you don’t see the More option, then you aren’t a global admin for your subscription.
- Find the people for whom you want to enable MFA. In order to see everyone, you might need to change the Multi-Factor Auth status view at the top.The views have the following values, based on the MFA state of the users:
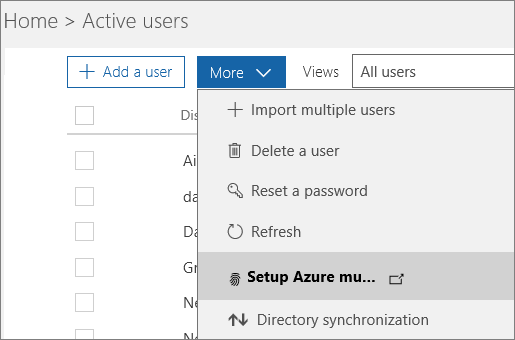
- Any Displays all users. This is the default state.
- Enabled The person has been enrolled in MFA, but has not completed the registration process. They will be prompted to complete the process the next time they sign in.
- Enforced The person may or may not have completed registration. If they have completed the registration process, then they are using MFA. Otherwise, theywill be prompted to complete the process the next time they sign in.
- Select the check box next to the people for whom you want to enable MFA.
- On the right, under quick steps, you’ll see Enable and Manage user settings. Choose Enable.
- In the
dialog box that opens,choose enable multi-factor auth.
Secure BOYD Mobiles and Company Phones
Almost everyone, even those employees without a company phone will use their own device to log into company emails and or sync calendars, contacts and documents just to stay on top of
Supported Devices: via O365
You can use MDM for Office 365 to secure and manage the following types of devices.
- Windows Phone 8.1+
- iOS 7.1 or later versions
- Android 4 or later versions
- Windows 8.1*
- Windows 8.1 RT*
- Windows 10**
- Windows 10 Mobile**
* Access control for Windows 8.1 and Windows 8.1 RT devices is limited to Exchange ActiveSync.
** Requires the device to be joined to Azure Active Directory and be enrolled in the mobile device management service of your organization.
If people in your organization use mobile devices that aren’t supported by Mobile Device Management for Office 365 , you might want to block Exchange ActiveSync app access to Office 365 email for those devices, to help make your organization’s data more secure. Steps for blocking Exchange ActiveSync: See Manage device access settings.
Access Management
Another great Microsoft Office 365 feature that will limit the access and flow of sensitive information across the organisation is access management. This includes user mailboxes, linked mailboxes, shared mailboxes and public folder mailboxes. User mailboxes may also include saved Skype for Business content, such as conversation histories. User mailbox content includes emails and email attachments, calendaring and free/busy information, contacts, tasks, notes, Groups, and inference data.
The access control list (ACL) that secures a mailbox contains an identity that is authenticated by Azure Active Directory at the tenant level. This is a great way to separate departments and management levels for document security and also productivity.
Encrypt Emails
Encrypting your email message in outlook will mean that it will convert from readable plain text into a scrambled text known as “ciphertext”. Only the recipients that have the private keys that match the public key used to encrypt the message can decipher the message for reading. This is extremely safe and a must when you’re constantly emailing out sensitive information.
Outlook supports two encryption options:
- S/MIME encryption – To use S/MIME encryption, the sender and recipient must have a mail application that supports the S/MIME standard. Outlook supports the S/MIME standard
- Office 365 Message Encryption (Information Rights Management) – To use Office 365 Message Encryption, the sender must have Office 365 Message Encryption, which is included in the O365 E3 license.
With the new Office
The Permissions button:

is replaced with the Encrypt button:

How to encrypt single messages:
- In the message that you’re composing, on the Options tab, in the More Options group, click the
dialog boxlauncher in the lower-right corner. - Click Security Settings, and then select the Encrypt message contents and attachments
check box . - Compose your message, and then click Send.
How to encrypt all outgoing messages:
- On the File tab, click Options > Trust Center > Trust Center Settings.
- On the E-mail Security tab, under Encrypted e-mail, select the Encrypt contents and attachments for outgoing messages check box.
- To change additional settings, such as choosing a specific certificate to use, click Settings.
If you require any further information on other methods of securing Office 365 please contact us we would be happy to assist.
Keep up with the conversation with Tech Patrol on:
Other Articles You May Enjoy:
















Share your thoughts in the Comments section: